Products Description
Definition and Types of Fake IDs
1. Definition of Fake IDs
A fake ID refers to any form of identification document that is not a genuine, legally issued ID, but rather one that has been forged, altered, or obtained through identity theft for fraudulent purposes. Fake IDs are typically used to conceal one's true identity, gain unauthorized access, or commit other illegal activities.
The primary types of fake IDs include:
Forged IDs: These are completely fabricated identification documents that closely mimic genuine IDs in appearance and content. Forged IDs are often made using advanced printing technology and materials, replicating the security features of real IDs.
Stolen Identity IDs: This involves using someone else's legitimate ID information to create a fake ID. For example, personal information is stolen and then used to modify or fabricate an ID to impersonate someone else. These fake IDs contain real personal data but are illegally produced and used.
2. Types of Fake IDs
Fake IDs can be categorized based on their method of creation and use:
(1) Forged IDs
Complete Forgery: IDs that are entirely created from scratch, including fake names, fictitious information, and fabricated security features. These IDs usually replicate every detail of a real ID, including images, text, stamps, and microtext.
Partial Forgery: Alterations made to a real ID to deceive, such as changing the birthdate or name on the ID to meet specific requirements.
(2) Counterfeit IDs
Close Counterfeits: IDs that are designed to be similar but slightly different from real IDs. These IDs may not fully meet the standards of a genuine ID but can still be used for some deceptive purposes.
Imitation IDs: IDs designed to imitate real IDs but lacking complete security features. These are often used for minor fraud, such as age verification scams.
(3) Stolen Identity Information
Identity Theft Fake IDs: Fake IDs created using stolen information from legitimate IDs, through alteration or fabrication. These IDs may closely resemble genuine ones in appearance but contain illegal alterations.
(4) Expired or Discarded IDs
Expired ID Reuse: Using expired real IDs for fraudulent activities, such as altering personal information and using the ID again. While technically the ID is still real, its use has been abused.
Identifying Fake IDs
To detect and prevent fake IDs, pay attention to the following features:
Printing Quality: Fake IDs may have lower-quality printing compared to genuine IDs, with blurry or inconsistent details.
Security Features: Genuine IDs usually have various security features like watermarks, fluorescent patterns, and laser engraving. Fake IDs may lack these features or imitate them poorly.
Information Consistency: Verify if the information on the ID matches other official records. Discrepancies or obvious errors may indicate a fake ID

Background Information on Fake ID Acquisition Channels
1. Underground Markets and Black Markets
Description: In underground markets or black markets, fake IDs are typically produced by illegal manufacturers. These manufacturers use advanced printing equipment and technology to forge identification documents that closely resemble real IDs. Examples include fake Social Security Numbers (US SSN), US fake green card, and Georgia Fake ID and Delaware Fake ID. These fake IDs are crafted to closely mimic real identification documents, including their appearance and security features.
Channels:
Dark Web Access: Underground markets and black markets are typically hidden on the dark web, which cannot be accessed through regular search engines. To access these markets, users need to use specific software, such as the Tor browser, which allows anonymous browsing of the dark web.
Illegal Trading Platforms: On these platforms, the trade of fake IDs and other illegal documents is conducted in hidden corners of the internet. Buyers and sellers conduct transactions through encrypted communication and hidden network addresses.
2. Online Black Markets
Description: Online black markets are typical platforms for illegal trading activities, including the sale of fake IDs. These platforms often offer various counterfeit documents and usually require cryptocurrency for payments to protect the anonymity of buyers and sellers.
Channels:
Dark Web Markets: These markets are located on the dark web, inaccessible through conventional networks. Buyers typically need to use specific cryptocurrencies (such as Bitcoin) for payments to enhance the secrecy of transactions.
Anonymous Communication: Transactions are usually conducted through encrypted communication tools to safeguard the privacy and identity of the parties involved.
3. Illegal Manufacturers
Description: Some individuals or small groups specialize in producing fake IDs. They may use professional printers, design software, and materials to replicate the appearance of official identification documents. These manufacturers may promote their services discreetly and conduct advertising and transactions through illegal channels.
Channels:
Social Media and Forums: Illegal manufacturers may advertise their services on social media platforms, dark web forums, or specialized criminal discussion groups.
Word of Mouth: In certain criminal circles, manufacturers may rely on word of mouth to attract customers, making their activities more clandestine.
4. Stolen Personal Information
Description: Criminals can obtain real personal information through phishing, data breaches, or other forms of fraud, and use this information to create fake IDs. These fake IDs may contain genuine personal data, but their production and use are illegal.
Channels:
Phishing: Criminals impersonate trusted institutions or individuals to trick victims into providing personal information, which is then used to produce fake IDs.
Data Breaches: Personal information obtained from data breaches can be used to create fake IDs. Sometimes, this leaked data is sold on the black market.
Tags:
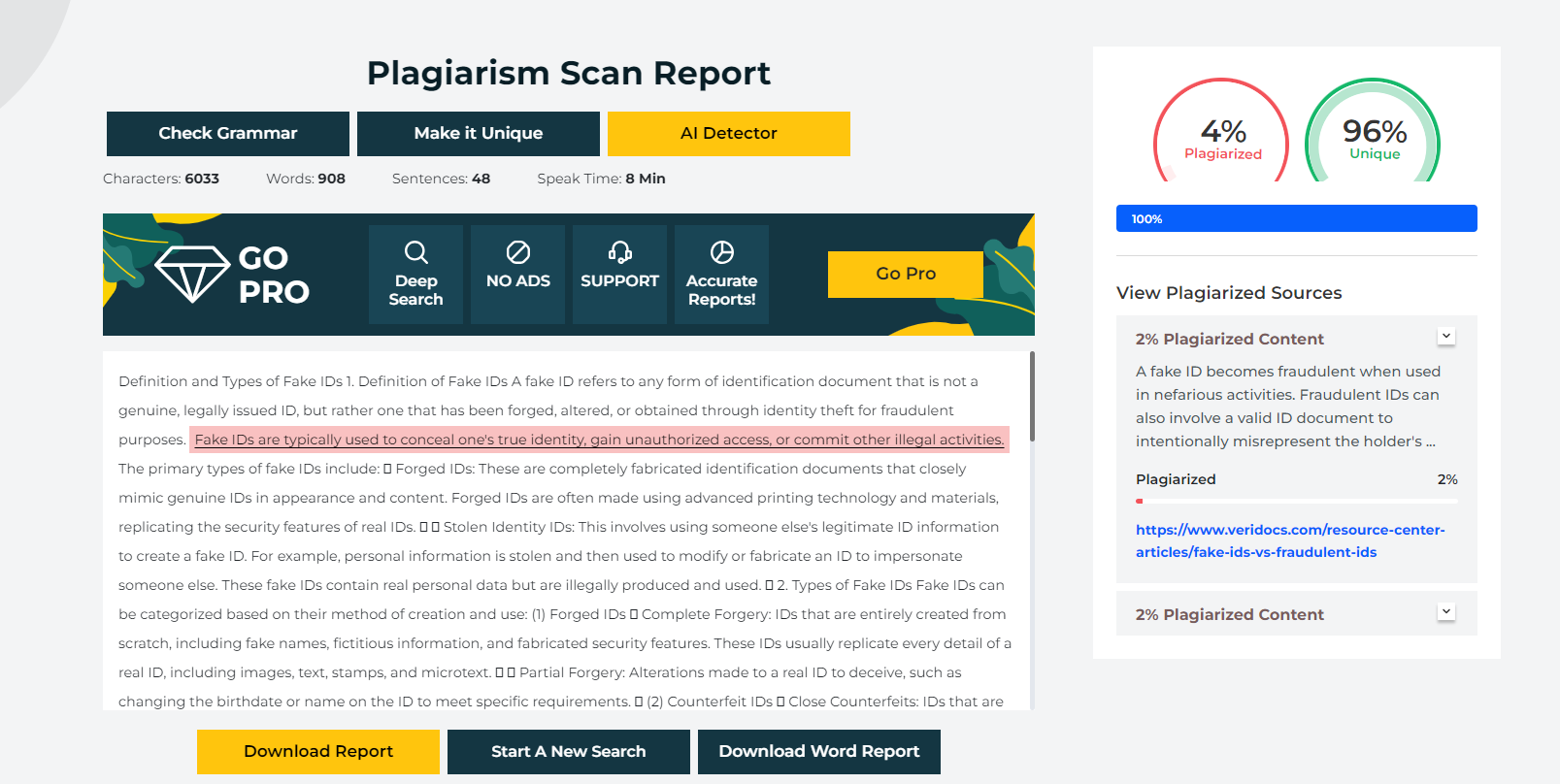
You like
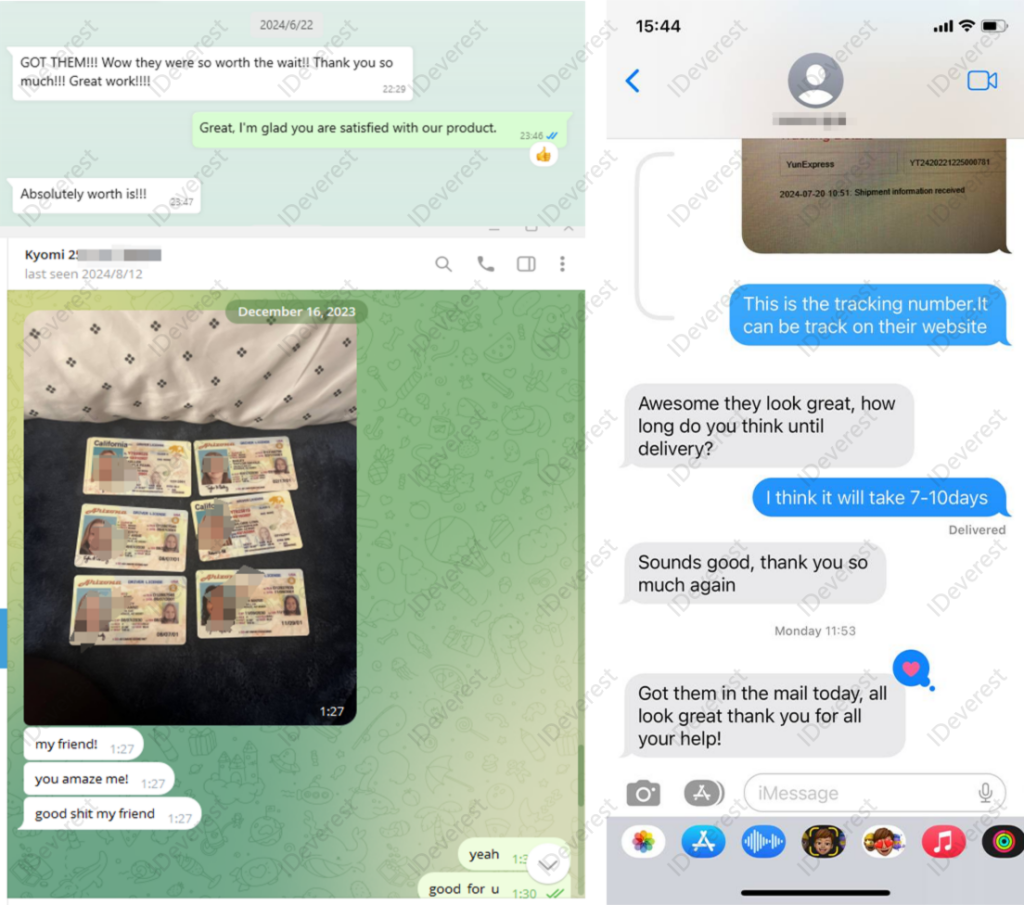
scannable Fake Arizona DL

scannable Fake New Jersey DL
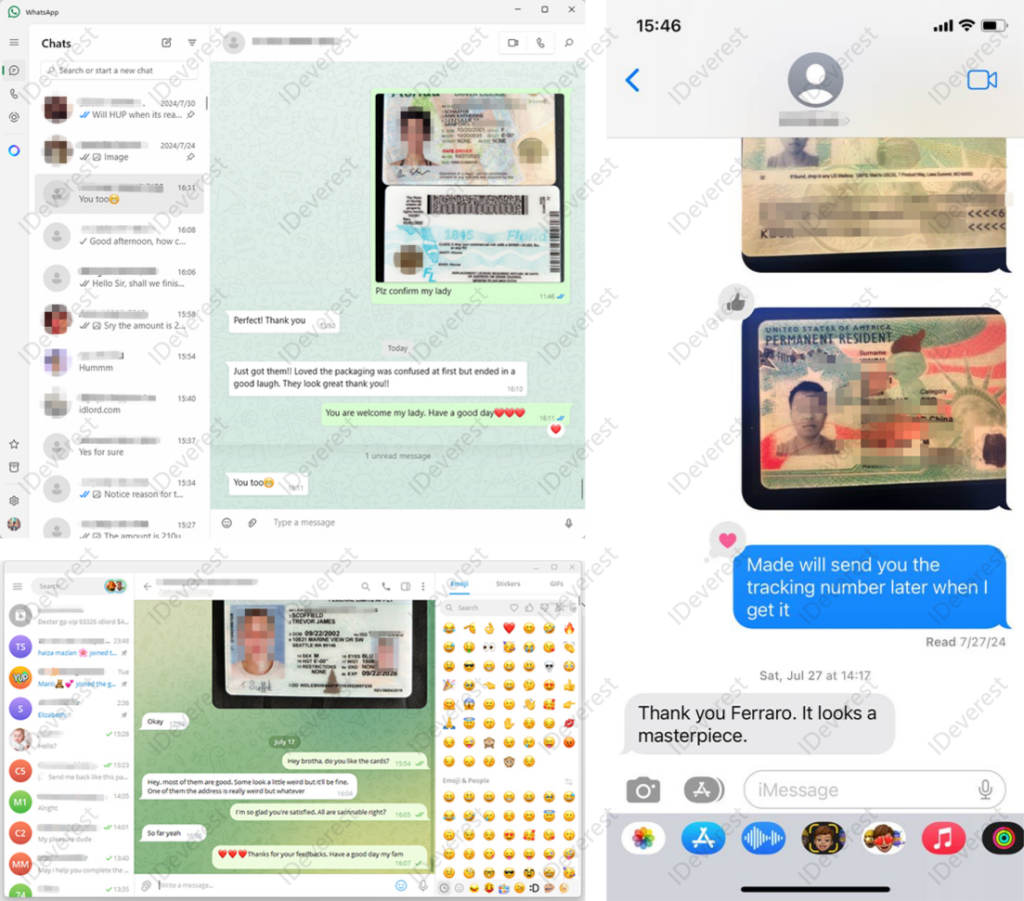
scannable Fake Florida DL

scannable Fake Georgia DL

